Note: Before a three letter federal agency shows up at my door let me be very clear here. The below described attack vector is proposed as a potential vulnerability for research and thought experiment purposes only. If I can think of this vector, so can people who are actually intent on using it. This blog post is intended as a conversation starter for possible ways to block this attack vector.
A Bit of Background
Have you ever wondered how the Internet is able to traverse enormous distances in the blink of an eye? How is it that you can have a real time video conversation with someone in China from the United States? How does the actual signal travel?
Many nontechnical people are stunned to find out that the answer isn’t “satellites.” Trust me, as someone who gets his internet from the geosynchronous satellite from Viasat because of my off the grid location, thank your preferred deity that the answer isn’t satellites.
Geosynchronous satellites are so far away that even at the speed of light (the speed of radio signals) the latency is unbearably slow. 0.5+ seconds. Yes, you know your internet connection sucks if you can reasonably express its latency in seconds.
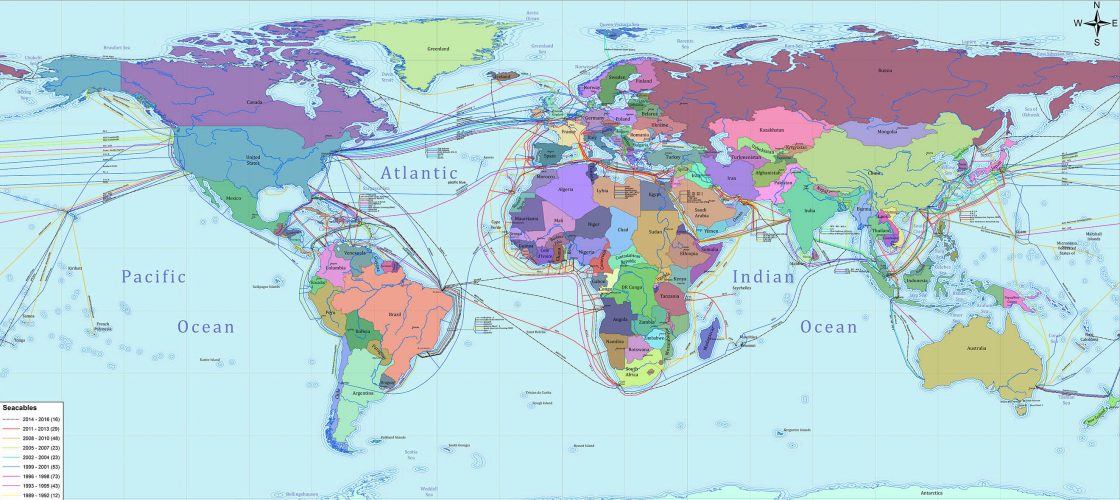
But if it’s not satellites, just how do we communicate with the rest of the world? Cables. Yes, good old cables. Well, technically very high and insanely fast fiberoptic cables, but cables nonetheless.
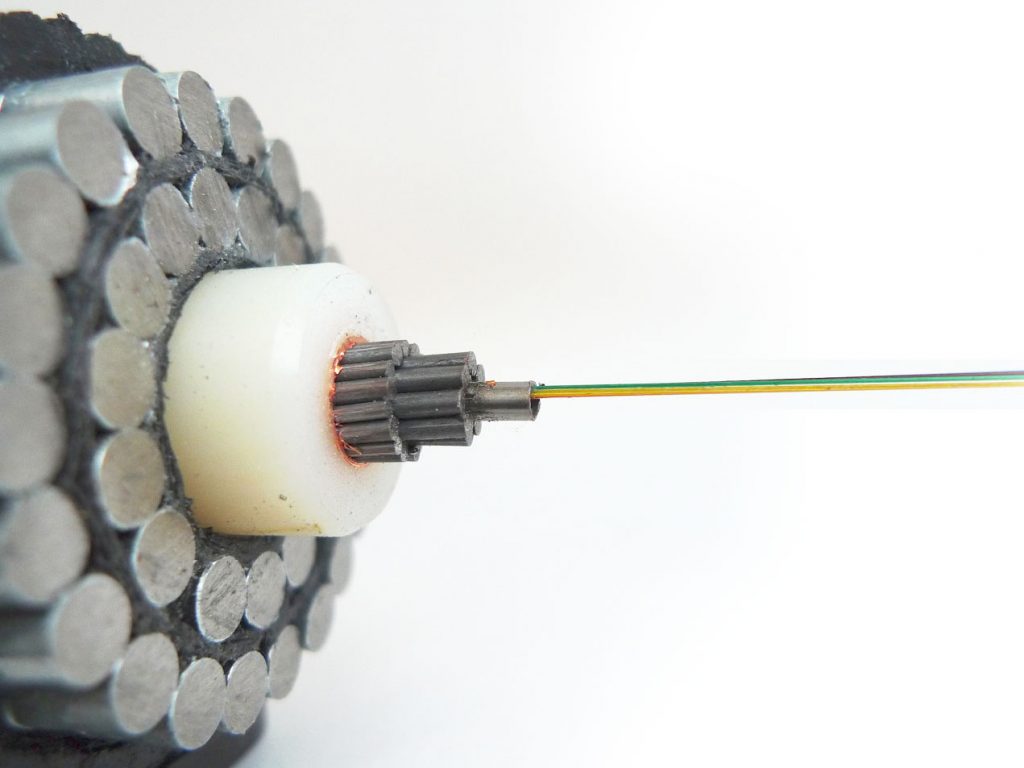
On land the cables are usually installed along side major freeways and roadways, but to connect the continents the cables are laid directly on the ocean floor.

And this system of cables is not nearly as redundant as you might think. Even in 2018 there are only a handful of cables that connect a major continent or country to the rest of the world, and of those there are newer primary cables that handle most of the load.
A Disconnected World
Now imagine if one day all of the sudden someone was to cut all of the fastest cables connecting various parts of the world, and fracture the internet. What would happen?
The stock market would crash immediately, of course, because they are a bunch of Panicky Petes, but the rest of the world wouldn’t do much better. Most of the satellite broadband would get very quickly overwhelmed and civilian trans oceanic communication would quickly grind to a halt. With any luck the various militaries of the world have a backup plan and private satellites to route their traffic. But the civilian internet will quickly crumble.
Even though most large corporations, like Google or Facebook, have redundant server farms in various geographic locations to comply with local laws and provide faster service to their clients, there are requests that still need to be fulfilled by servers located in United States in order for those services to function properly. Even large redundant services will eventually grind to a halt without persistent communication.
I will let the reader imagine the horror that the world will be without Google and Netflix, as such is just too horrifying to describe in words.
What About Redundancy?
I know what you are going to say. You vaguely remember that the www in URLs stands for “world wide web,” and somewhere no doubt you read that if one link in the web breaks, the internet can reroute the traffic through other links in the web. So why am I fear-mongering?
You are right, if one link in the web breaks, then the internet will be happy to reroute the traffic through other available links. In fact, that happens all the time. Individual internet cables break for all kinds of reasons, but our internet doesn’t crumble to pieces as a result.
But what if 2/3rds of them break, all at the same time, in a coordinated attack? What happens then? Will the remaining links be able to handle the remaining traffic? Will the central routers be able to even find an effective path? Just because the Internet is a web, it doesn’t necessarily mean that all parts of it are able to communicate with each other equally.
Ok, sure, if we can take out multiple cables at the same time, say 60 or 80 of them, then the internet may indeed come crumbling. But what are the chances that someone would be able to pull that off? They would need 60 crews with boats and divers stationed all over the world. Who has the resources for that? Ok, maybe the Russians, but who else?
Well, let’s look at these 2 attack vectors and you be the judge.
Timed Attack Vector
Imagine you are Dr. Evil, and you want to extort the world for “One Hundred Billion Dollars.” What would you do? Ok, also imagine that you were a competent evil mastermind.

So you need to sever the connection on 60 to 80 internet cables, all at the same time, and you don’t want to have 60 to 80 conspicuously positioned boats waiting for your signal. What do you do?
Well, in today’s day and age you don’t actually need much. A high capacity battery, a timing circuit, and some thermite or a suitable shaped explosive charge.
All you have to do is package your explosive load with a detonator and timer into a waterproof case with neodymium magnets attached to the outside of the case to clamp the case to the side of the underwater cable (underwater cables have metal cladding).
To position the explosive case you will need to make a remote controlled underwater rover. With off the shelf parts and 3D printing you can make such a robot relatively easily. Of course, if you are Dr. Evil, and have access to Evil Amazon, you can also easily buy a ready-made research robot to do the job.
You will also need to procure some high quality sonar and magnetometer equipment, but again, if you are Dr. Evil (or can use eBay) this should not be an issue. You will use this equipment to locate the various underwater cables.
That’s about it! Well, and you’ll need to rent a fishing boat with sonar and magnetometer equipment to detect the cables. Under the assumed identity of the Fisherman you would go out and attach these explosive cases to 60 to 80 cables throughout the world. Of course such an endeavor will take time. But that’s not a problem. You can always set the go time for 6 months or even several years from the start of the project. You have to estimate when you will be ready, and when you are, it’s go time.
Sounds easy. No? And that’s scary. Honestly, I have thought about this for a while, and I can’t see any reason why this would be any more complicated than what I have laid out above. I hope it is, but I just don’t see how. Long running precise timers are available, batteries are available, suitable explosives can be easily manufactured by people with minimal chemistry knowledge, and the rest is just a matter of money, and minimal amount of money at that.
Remote Controlled Attack Vector
One problem with the above method, however, is the lack of control. Sure, you have control about the precise date and time the cables will be severed, but what if you want to postpone, cancel, or accelerate the attack. After all, if you are Dr. Evil, if you do blackmail the world for one hundred billion dollars and they actually pay, you don’t want to actually blow up the internet. Or do you….?
A controlled attack would be more desirable (if you are Dr. Evil or another super villain), and actually relatively easy to achieve as well through scheduled communication. It would require a more complex design for the explosive case, but still well within the capability of any graduate level mechanical engineer.
You would design the case with much larger battery capacity, and electrically operated spindle, and a buoy attached by a synthetic fishing line like cable.
The buoy would have inside of it an Iridium (or other satellite communications company) modem, an embedded computer, a bluetooth link, a rechargeable battery and wireless charging circuit.
The buoy would sit in a cradle inside the case most of the time. Once a week, month, or at a preprogrammed time the spindle would unwind the tether allowing the buoy to float to the surface. At the surface the buoy would establish satellite communication, connect to command and control server, download latest instructions, and then it would get automatically reeled back in by the spindle into the cradle.
The information would be dumped from the buoy to the main computer inside the case via wireless link and the battery inside the buoy would be wirelessly charged for the next trip to the surface. The buoy would be limited in the number of trips it can make to the surface by the capacity of the main battery. But with modern Lithium ion batteries I estimate that even a modestly sized system would be able to perform at least 100 trips to the surface without an issue.
There are some questions about how efficient of a satellite connection the buoy would be able to establish when floating on the surface of the water, but even if that’s an issue, it could be easily solved with a slightly more complex design.
The point is, with only a little effort and design, Dr. Evil can build himself a remote controlled internet cable severing system. The system cannot be triggered at a moment’s notice, but it can be set to detonate at a predetermined date and time remotely, and the detonation can be cancelled or postponed remotely as well.
Conclusion
The 2 scenarios above are scarily simple to implement with determination and relatively modest funding. I posted this blog post because these attack vectors have been floating around in my head for a while now, and I would love to see what others think.
Is there something that’s being currently done to prevent just such a scenario? Can something be done?
I have some of my own ideas, but they aren’t well formed yet, so stay tuned, I’ll be sure to post when I have something interesting.